Herkese Merhaba,
Fortigate’ in Multiple İnterfaces Policies özelliğinden bahsedeceğiz. Ne işimize yarar diye düşünürsek normalde source ve destination interface eklediğimiz kuralları düşünün ve onu sources ve destinations olarak değiştirelim kısaca kural kalabalığından kurtarıyor diyebiliriz.
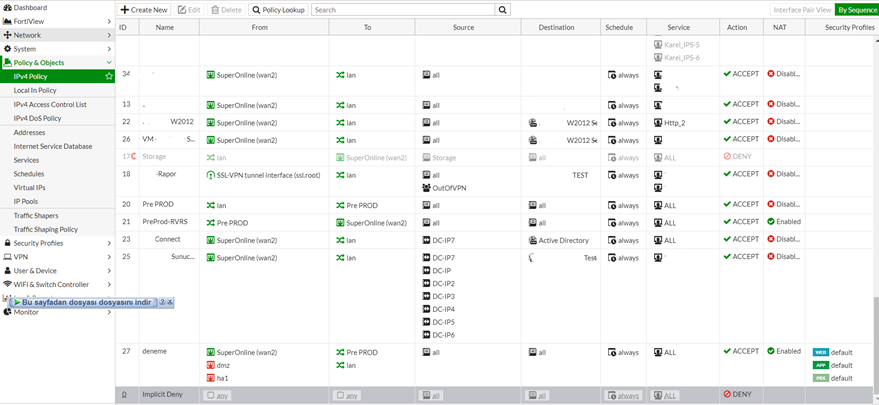
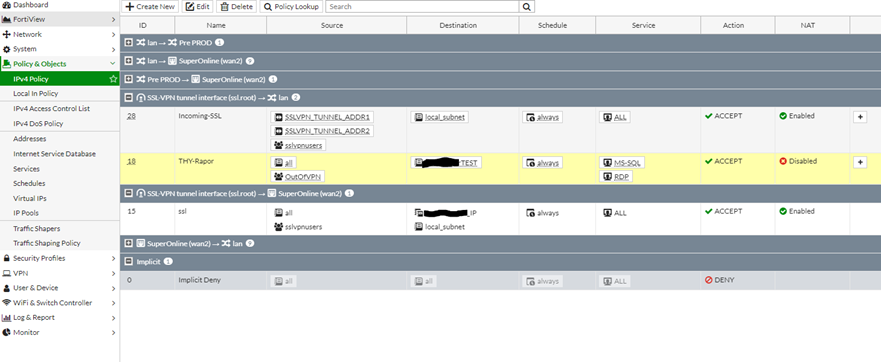
Dezavantaj olarak ise (makalenin sonunda farkı göstereceğim) kural ekranımızdaki default ta gelen INTERFACE PAIR görünümünü kapatıyor ve BY SEQUENCE moduna geçiyor. Çünkü kuralımız tek bir interface olmayacağı için bu ayarlama yapılamıyor.
Örnek olarak bir yere VPN vermek istiyorsunuz. Port1 ve Port2 interfaceleri ayrı networkler olduğunu düşünelim. Bunun için VPN to Port1 ve VPN to Port2 diye 2 ayrı kural yapmam lazım. Bu anlatacağım özellik sayesinde tek kural ile VPN to Port1 and Port2 yapabiliyor olacağım ve tek kural da işimi çözmüş olacağım .
Nasıl yapıldığına geçelim;
İlk olarak System > Feature Select sayfasına gelip MULTIPLE INTERFACE POLICIES özelliğini aktif ediyoruz.
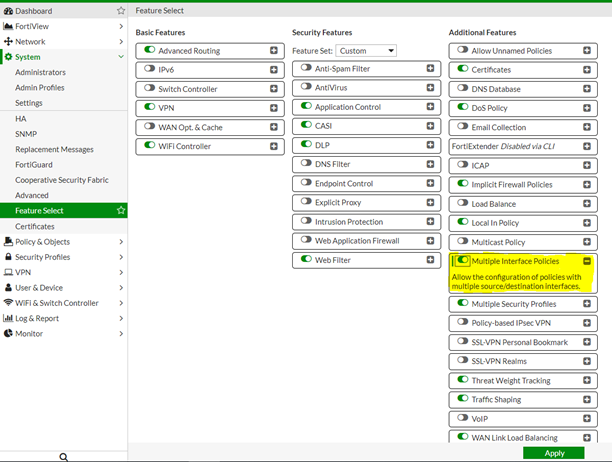
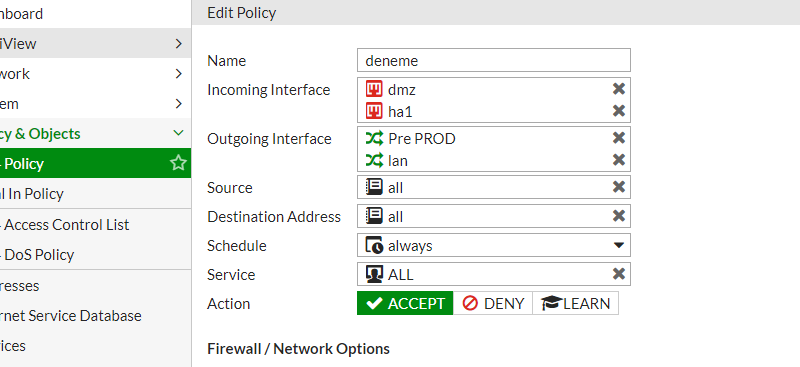
Bunu yaptıktan sonra yeni bir kural oluşturuyoruz.
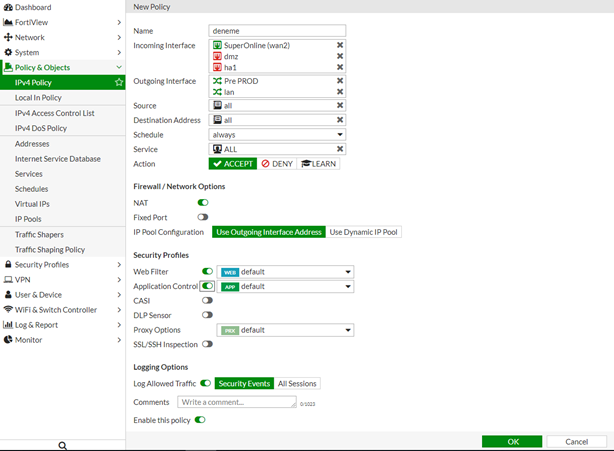
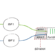
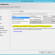
Gördüğünüz gibi birden fazla source ve destination interface e sahip bir kural oluşturduk ok diyerek kaydediyoruz.
Ve gördüğünüz gibi kuralımız belirlediğimiz portlarla oluştu.
İşinize Yaraması Dileğiyle..
BY SEQUENCE görünümü
INTERFACE PAIR görünümü


Leave a Reply